
As always we first start with nmap scan to find which ports are open and which services running on those ports.
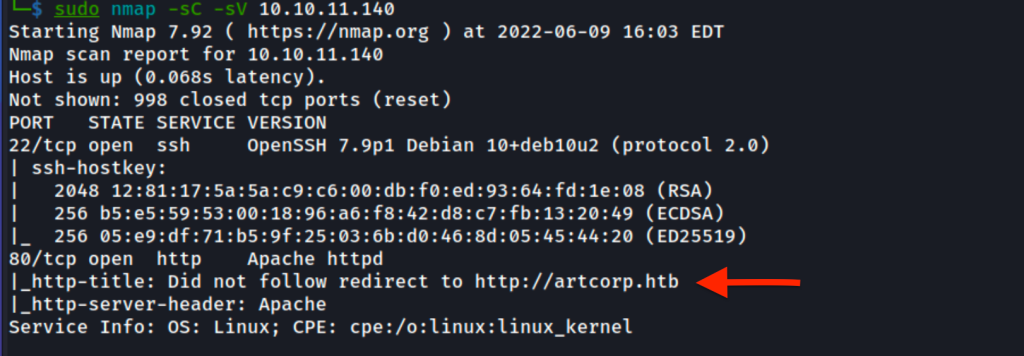
-sV: to detect service versions
We add it into our hosts file.

Let’s visit artcorp.htb

We do not find anything useful.
Let’s run ffuf scan to get more information.
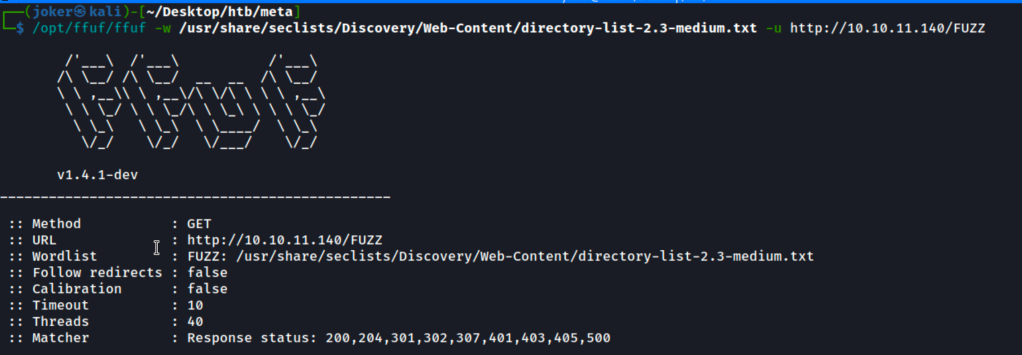
ffuf scan reveals that there is a subdomain called “dev01”
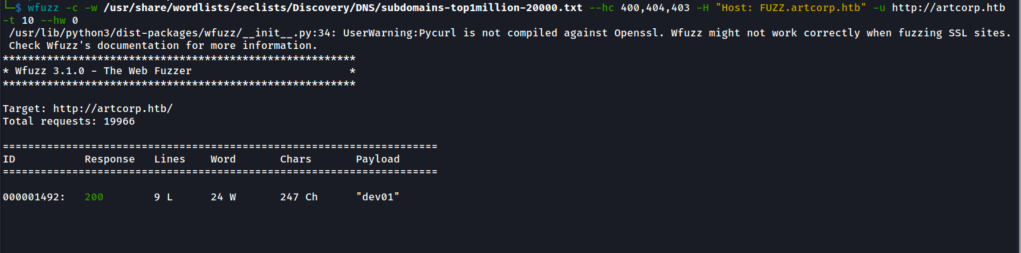
Add it into the hosts file.

And visit the page.

Visit the link.
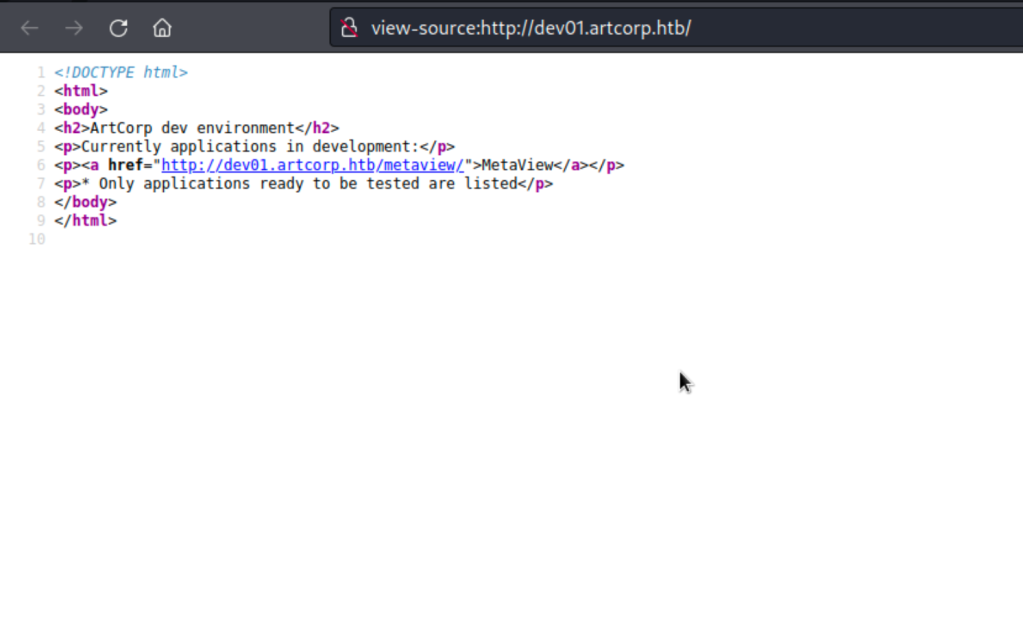
We have some idea what this is about. The page prompts us to upload an image to display the corresponding its metadata, so it is a tool for extracting image’s metadata.
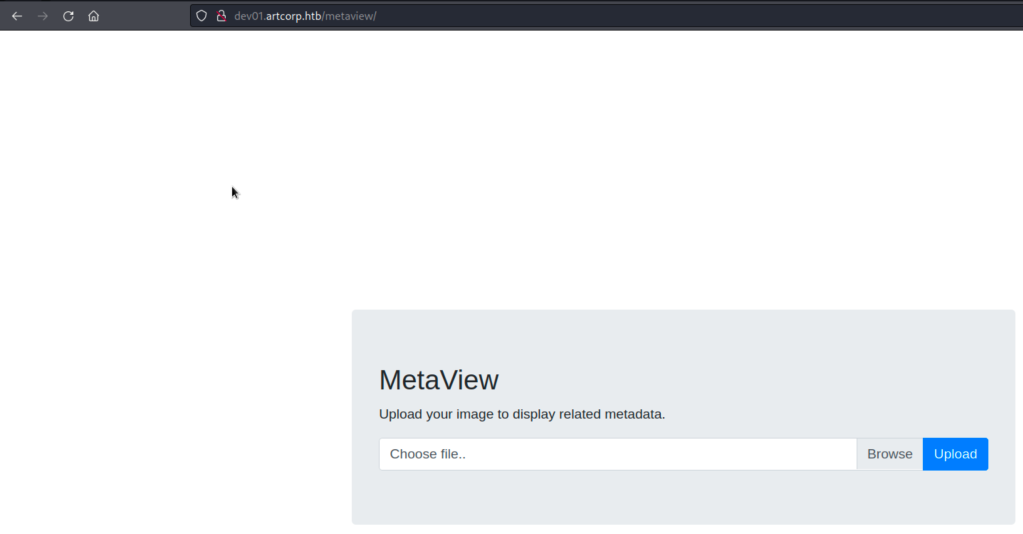
Upload a simple image file to see the response.

The output is as we expected. Looks like exiftool output.

We search exiftool on the internet whether there is a vulnerability that we can use and take the advantage in any version of exiftool.
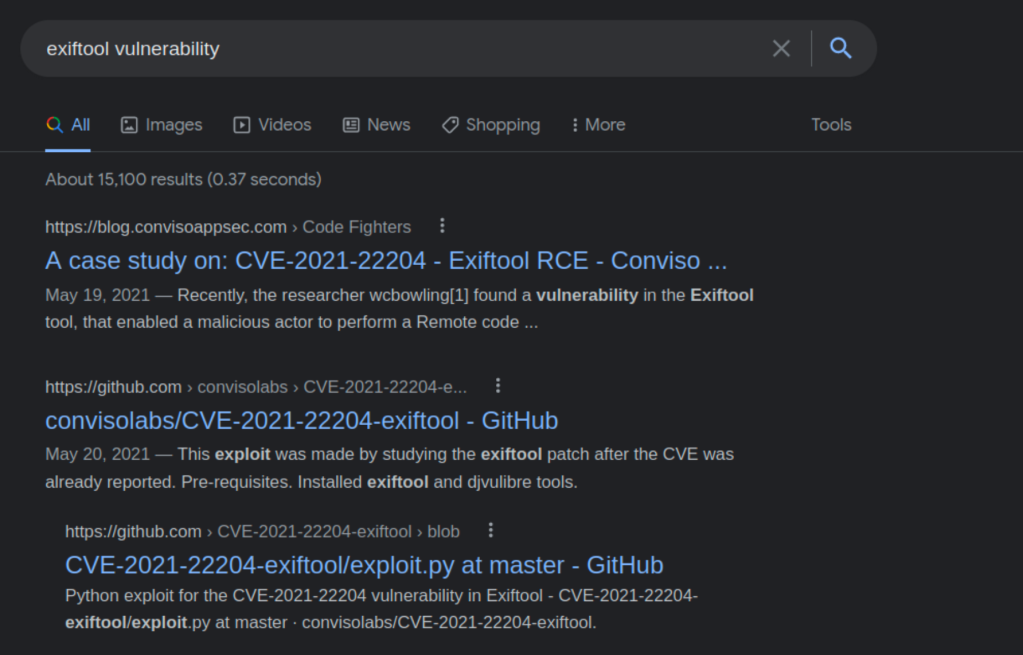
Choose to use CVE-2021-22204 vulnerability to exploit exiftool.

Clone the source code into our local repo.

The remote code execution vulnerability will be triggered by uploading malicious format file in the background.
Edit the listening host and port.

netcat is listening on port 9002.

Execute the code and get the malicious file.

Upload the file.

And get the shell.

Upgrade the shell to a full interactive shell.

We do not have permissions to open and read the user.txt file and .ssh directory.

So, we must be the user thomas! To do so, what is the first step? Enumeration, exactly.
Let’s create a http server in python to upload a linux enumeration script called linpeas.sh


We get an interesting executable file. Worth to review it.

The script simply converts the image to png format by using mogrify.

Get the mogrify version.

And search the version on the internet.

We visit the link showing below. The post reveal that the vulnerability is due to the incorrect handling of an "authenticate” parameter that allow users to set a password for encrypted PDFs. Since the user-controlled password was not properly sanitised and it was therefore possible to inject additional shell commands.

We use CVE-2020-29599 vulnerability in order to escalate our privilege on the machine.
Create the poc.svg file on the local machine.

And download the file to /dev/shm where placing it in a directory with executable permissions.
Copy the file to the “/var/www/dev01.artcorp.htb/convert_images/” directory. It will convert the file and generate a file called 0wned in the directory.

The file is created in a short time.

Good. The code execution is successful.

The file belongs to thomas. So, we go over in this context. Let’s try to retrieve thomas’ ssh private key. To do so, we make a small edit on the script.

Download edited one and run the same process.

Great! We get the ssh private key.

It looks a bit awkward.

Because the private key is a bit complicated the system does not allow us login.

After modify the private key, we successfully login as user thomas.

And get the user flag.

Time to escalate our privilege to root.
First thing first we check that what commands thomas can execute as root.

Let’s execute neofetch.


We search directories related to neofetch and see a config things. We may edit that config file.

We can edit it as user thomas.

Add the reverse shell payload inside of it.

XDG home environment must be reset in order to new configuration, which contains our reverse shell payload, works.
After some research we get how to do it.

netcat is listening on port 9000.

Everything is ready. We should be quick because the config.conf file reset itself in a short time.
1. Add the reverse shell payload.
2. Reset the XDG environment
3. Execute neofetch

Boom! We are successfully in and get the root flag.

Thank you for your time.